Automation is a key ingredient in any successful DevSecOps implementation. Given the complexities of modern software development, relying on manual testing will slow even the most organized and strategic organizations. The right DevSecOps tools enable organizations to implement DevSecOps principles like agility, comprehensive testing and monitoring, tight feedback loops, security throughout the SDLC, and, ultimately, the delivery of high-quality software.
Of course, as organizations have increasingly embraced DevSecOps strategies, there’s also been a spike in the number and types of tools that support DevSecOps initiatives. In this blog, we’ll take a look at five particularly important categories of DevSecOps tools and their use cases.
(Note: This is not intended to be an exhaustive list of important DevSecOps tools, nor is it intended to be a ranking of the most important tools. Rather, this post will explore five commonly used DevSecOps tools, including their function and how they support DevSecOps objectives. This post is based in part on the U.S. government’s DevSecOps Fundamentals Guidebook: DevSecOps Tools & Activities, which offers a more comprehensive overview of DevSecOps tools and how they support DevSecOps practices).
1. Software Composition Analysis (SCA)
Given the fact that open source software makes up over 90% of the codebase of modern applications, SCA has become an indispensable DevSecOps tool.
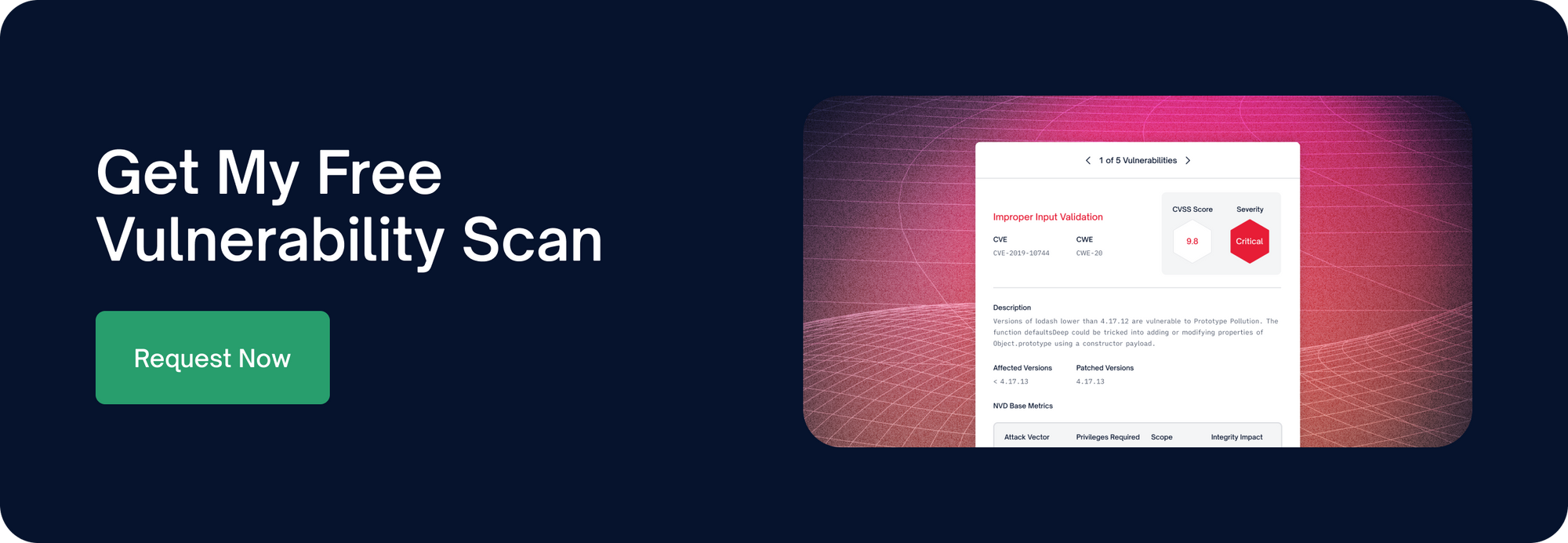
Software composition analysis (SCA) tools scan applications to detect and address issues (security vulnerabilities, problematic OSS licenses, and quality issues) in open source code. SCA solutions also offer reporting functionality, including the ability to generate a software bill of materials.
If and when SCA does identify a vulnerability, it provides a host of information (including severity score, inclusion path, and remediation guidance) to help users properly address the issue.
For the open source license compliance use case, SCA inventories the different licenses involved in your code, flagging any components with licenses that violate an organization’s compliance policies.
Finally, modern SCA tools also help teams implement the key DevSecOps principle of delivering quality software. SCA offers code quality and provenance checks, helping users identify and upgrade outdated and/or poorly maintained software components.
2. Static Application Security Testing (SAST)
SAST refers to a set of tools that scan codes (source code, binary code, byte code) in a non-running (read: static) state. SAST flags weaknesses in the code it scans, effectively surfacing common issues like CWE-79 (cross-site scripting), buffer overflow errors, SQL Injection, and more.
Much like SCA, SAST flags vulnerabilities and offers remediation guidance. Both tools analyze source code/binaries as opposed to running applications. And, both SCA and SAST are frequently used during the “build” stage of the software development lifecycle, in line with the “shift-left” principle of conducting security testing as early as possible in the SDLC.
There are several significant differences between SCA and SAST, however. While SCA identifies vulnerabilities in open source code, SAST detects vulnerabilities in proprietary code. And, as you might expect, open source license compliance is not a SAST use case. DevSecOps teams often use SCA and SAST in a complementary manner.
3. Dynamic Application Security Testing (DAST)
In contrast to SAST and SCA, DAST (Dynamic Application Security Testing) tests for vulnerabilities in a running application. As such, it’s used later in the software development lifecycle.
DAST does not require access to source code. Instead, DAST tools detect vulnerabilities in a running application by (safely) injecting malicious inputs to identify potential security vulnerabilities within the application. A DAST tool will make HTTP requests and uncover issues like SQL injections, OS injections, and cross-site scripting errors. It also finds bugs that are important to application security contexts, like security headers, cookie safety, content security policies, and X-Frame-Options.
There’s no language dependency with DAST tools because they test the running app, however you compile it. DAST also takes into account the context of how the application works: It tests the running application with bad inputs to see how the application behaves. Security teams often use DAST tools as part of their application security suites along with SAST, SCA, and more.
4. Automated Testing Tools
The days of large, dedicated QA teams are a thing of the past for organizations with successful DevSecOps implementations. As the U.S. government’s DevSecOps Fundamentals Guidebook puts it: ”Testing is about automation, and testers will need to become coders of that automation.”
Although some manual testing work will still be required — it’s not possible to automate every part of every test — the majority can be automated. For example:
- Unit tests: Unit tests analyze individual units of code to make sure they perform as expected. Unit testing tools tend to be language-specific.
- Integration tests: Integration tests are performed after unit tests and deal with the interaction between units of code. Again, many of these tests are language-specific.
- System tests: System tests are performed after integration tests and analyze the entire application. System testing tools analyze areas like usability, reliability, scalability, and more.
Performance testing, regression testing, and acceptance testing are also among the areas that can be automated.
5. Issue Tracking System
The final tool we'll discuss is one that most teams are likely already familiar with: issue tracking software. Issue tracking systems support several key DevSecOps phases and activities.
Key characteristics of issue tracking tools include:
- Automation: Improves engineering efficiency by automating processes like closing issues, notifying customers, assigning issues, and more
- Issue resolution tracking and history: Provides visibility and structure to enable efficient bug management. Also creates a record of activities related to issue resolution.
- Change management: Equips stakeholders with visibility into new feature development. Offers interactive workflows and roadmaps to support planning and development.
- Prioritization management: Enables teams to easily (i.e. drag and drop) prioritize different fixes and activities so that they continuously address the most important items
- Automated reporting capabilities: Offers a consolidated view of created vs. resolved issues, resolution velocity, development velocity, and other important metrics
There are a variety of free and paid issue tracking tools on the market today — Jira and GitHub Issues are among the most popular (and both have strong integrations with FOSSA’s SCA tool).
DevSecOps Tools: The Bottom Line
Successful DevSecOps implementations require effective DevSecOps tools. And, the tools we discussed in this blog have an important role in helping organizations automate software testing and management.
Leading enterprises like Uber, Twitter, Slack, and Verizon use FOSSA’s software composition analysis tool to automate the inventory and management of open source code components. For more information on how FOSSA SCA can help your organization, get in touch with our team.


